July 29, 2025 by The Korea Advanced Institute of Science and Technology (KAIST)
Collected at: https://techxplore.com/news/2025-07-vulnerability-packet-paralyze-smartphones.html
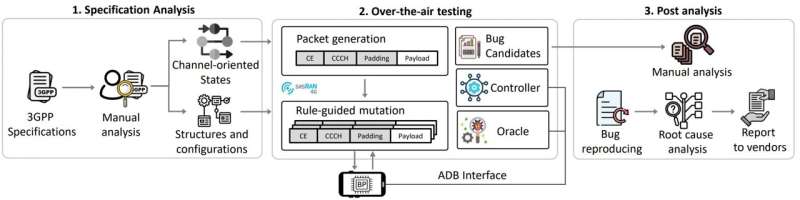
Smartphones must stay connected to mobile networks at all times to function properly. The core component that enables this constant connectivity is the communication modem (baseband) inside the device. KAIST researchers, using their self-developed testing framework called LLFuzz (Lower Layer Fuzz), have discovered security vulnerabilities in the lower layers of smartphone communication modems and demonstrated the necessity of standardizing mobile communication modem security testing.
Professor Yongdae Kim’s team from the School of Electrical Engineering at KAIST, in a joint research effort with Professor CheolJun Park’s team from Kyung Hee University, have discovered critical security vulnerabilities in the lower layers of smartphone communication modems. These vulnerabilities can incapacitate smartphone communication with just a single manipulated wireless packet (a data transmission unit in a network). In particular, these vulnerabilities are extremely severe as they can potentially lead to remote code execution (RCE)
The research team utilized their self-developed LLFuzz’ analysis framework to analyze the lower layer state transitions and error handling logic of the modem to detect security vulnerabilities. LLFuzz was able to precisely extract vulnerabilities caused by implementation errors by comparing and analyzing 3GPP standard-based state machines with actual device responses.
The research team conducted experiments on 15 commercial smartphones from global manufacturers, including Apple, Samsung Electronics, Google, and Xiaomi, and discovered a total of 11 vulnerabilities. Among these, seven were assigned official CVE (Common Vulnerabilities and Exposures) numbers, and manufacturers applied security patches for these vulnerabilities. However, the remaining four have not yet been publicly disclosed.
While previous security research primarily focused on higher layers of mobile communication, such as NAS (Network Access Stratum) and RRC (Radio Resource Control), the research team concentrated on analyzing the error handling logic of mobile communication’s lower layers, which manufacturers have often neglected.
These vulnerabilities occurred in the lower layers of the communication modem (RLC, MAC, PDCP, PHY), and due to their structural characteristics where encryption or authentication is not applied, operational errors could be induced simply by injecting external signals.
The research team released a demo video showing that when they injected a manipulated wireless packet (malformed MAC packet) into commercial smartphones via a software-defined radio (SDR) device using packets generated on an experimental laptop, the smartphone’s communication modem (baseband) immediately crashed
The video shows data being normally transmitted at 23MB per second on the fast.com page, but immediately after the manipulated packet is injected, the transmission stops and the mobile communication signal disappears. This intuitively demonstrates that a single wireless packet can cripple a commercial device’s communication modem.
The vulnerabilities were found in the modem chip, a core component of smartphones responsible for calls, texts, and data communication, making it a very important component.
- Qualcomm: Affects over 90 chipsets, including CVE-2025-21477, CVE-2024-23385.
- MediaTek: Affects over 80 chipsets, including CVE-2024-20076, CVE-2024-20077, CVE-2025-20659.
- Samsung: CVE-2025-26780 (targets the latest chipsets like Exynos 2400, 5400).
- Apple: CVE-2024-27870 (shares the same vulnerability as Qualcomm CVE).
The problematic modem chips (communication components) are not only in premium smartphones but also in low-end smartphones, tablets, smartwatches, and IoT devices, leading to the widespread potential for user harm due to their broad diffusion.
Furthermore, the research team experimentally tested 5G vulnerabilities in the lower layers and found two vulnerabilities in just two weeks. Considering that 5G vulnerability checks have not been generally conducted, it is possible that many more vulnerabilities exist in the mobile communication lower layers of baseband chips.
Professor Yongdae Kim explained, “The lower layers of smartphone communication modems are not subject to encryption or authentication, creating a structural risk where devices can accept arbitrary signals from external sources. This research demonstrates the necessity of standardizing mobile communication modem security testing for smartphones and other IoT devices.”
The research team is continuing additional analysis of the 5G lower layers using LLFuzz and is also developing tools for testing LTE and 5G upper layers. They are also pursuing collaborations for future tool disclosure. The team’s stance is that “as technological complexity increases, systemic security inspection systems must evolve in parallel.”
First author Tuan Dinh Hoang, a Ph.D. student in the School of Electrical Engineering, will present the research results in August at USENIX Security 2025.
More information: Tuan Dinh Hoang et al. LLFuzz: An Over-the-Air Dynamic Testing Framework for Cellular Baseband Lower Layers, syssec.kaist.ac.kr/pub/2025/LLFuzz_Tuan.pdf

Leave a Reply